| CPC H04L 9/3213 (2013.01) [G06F 9/547 (2013.01); H04L 9/3073 (2013.01)] | 30 Claims |
|
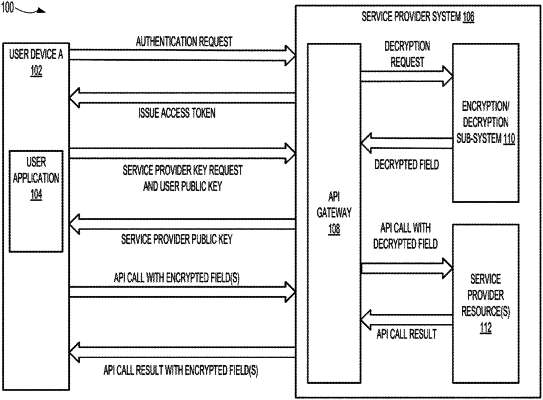
1. A computer-implemented method, comprising:
generating an access token based on a successful authentication of a user application session;
transmitting the access token, wherein a user application uses the access token to make application programming interface (API) calls;
receiving a key request, the key request including the access token and a user public key;
generating, in response to the key request, a service provider key pair including a service provider public key and a service provider private key;
transmitting the service provider public key, wherein when the service provider public key is received at a user device, the user device uses the service provider public key to encrypt fields in the API calls;
receiving an API call including the access token and an encrypted field;
decrypting the encrypted field using the service provider private key to obtain a decrypted API call; and
performing an API action based on the decrypted API call.
|