| CPC H04L 9/088 (2013.01) [G06F 1/04 (2013.01); H04L 9/0869 (2013.01)] | 19 Claims |
|
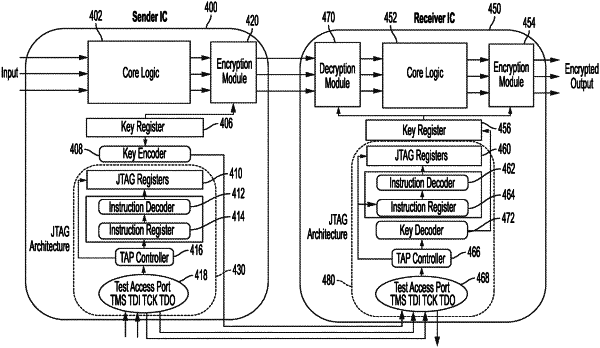
1. A method for delivering data from a first integrated circuit (IC), the method comprising:
generating, by the first IC, a seeding key during a start-up phase of the first IC;
generating, by a linear-feedback shift register disposed in the first IC, a key based at least in part on the seeding key, wherein the key is one of a set of keys generated by loading the seeding key to the linear-feedback shift register disposed in the first IC;
encrypting, by the first IC, the data using the key to generate encrypted data;
encoding, by the first IC, the seeding key to obtain encoded seeding key;
transmitting, by the first IC, the encoded seeding key to a second IC, wherein the encoded seeding key is decoded to obtain decoded seeding key, wherein the key is generated by a linear-feedback shift register disposed in the second IC based at least in part on the decoded seeding key, and wherein the linear-feedback shift register disposed in the second IC performs the same operation as that of the linear-feedback shift register disposed in the first IC; and
transmitting, by the first IC, the encrypted data to the second IC, wherein the encrypted data is decrypted using the key.
|