| CPC H04L 9/0861 (2013.01) [H04L 9/0819 (2013.01); H04L 9/3268 (2013.01)] | 20 Claims |
|
1. An apparatus for validating user data, the apparatus comprising:
at least a processor;
and a memory communicatively connected to the at least a processor, the memory containing instructions configuring the at least a processor to:
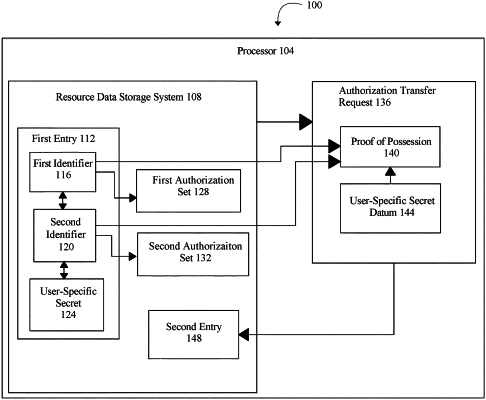
identify, in a resource data storage system, a first entry cryptographically linking a first identifier, a second identifier, and a cryptographic commitment to a user-specific secret, wherein:
the first identifier is associated with a first authorization set, the first authorization set comprising lost user data to be recovered;
and the second identifier is associated with a second authorization set;
receive, from a user, an authorization transfer request including an indication of the first identifier, a proof of possession of the second identifier, and a user-specific secret datum, wherein the user-specific secret datum is based on the user-specific secret, and the user-specific secret datum is evaluated against the user-specific secret to validate user identity;
evaluate the authorization transfer request as a function of the first entry, the proof of possession of the second identifier, and the user-specific secret datum, wherein evaluating the authorization transfer request comprises verifying a lost status for the first identifier;
transfer the first authorization set of the first identifier to the second identifier as a function of the first identifier, the proof of possession of the second identifier, and the user-specific secret datum; and
responsive to evaluating the authorization transfer request, recover the first authorization set by generating a second entry associating the second identifier with the first authorization set, wherein generating the second entry comprises dissociating the first identifier from the first authorization set such that the first identifier may no longer be able to access the first authorization set, thereby treating the first identifier lost.
|