| CPC H04L 9/008 (2013.01) [G06F 9/3887 (2013.01)] | 16 Claims |
|
1. A computer-implemented method comprising:
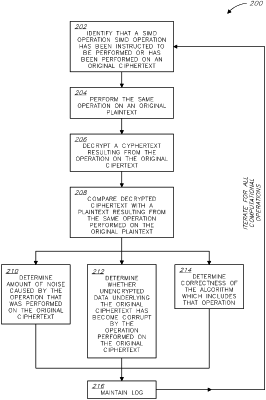
in response to identifying that a Single Instruction, Multiple Data (SIMD) operation has been instructed to be performed or has been performed by a Fully-Homomorphic Encryption (FHE) software on one or more original ciphertexts, performing the following steps, automatically:
(a) performing the same operation on one or more original plaintexts, respectively, that are each a decrypted version of one of the one or more original ciphertexts;
(b) decrypting a ciphertext resulting from the operation performed on the one or more original ciphertexts;
(c) comparing the decrypted ciphertext with a plaintext resulting from the same operation performed on the one or more original plaintexts; and
(d) based on said comparison, performing at least one of:
determining an amount of noise caused by the operation performed on the one or more original ciphertexts,
determining whether unencrypted data underlying the one or more original ciphertexts has become corrupt by the operation performed on the one or more original ciphertexts, and
determining correctness of an algorithm which includes the operation performed on the one or more original ciphertexts;
wherein the method is implemented as an implementation of an abstract Application Programming Interface (API) having a set of operators identical to a set of operators of the FHE software; and
wherein the abstract API comprises an abstract class programmed to interface with the FHE software so as to: provide instructions to the FHE software to perform the decryption of step (b), and receive the decrypted ciphertext from the FHE software.
|