| CPC H04L 63/1483 (2013.01) [G06F 16/2255 (2019.01); G10L 15/10 (2013.01); G10L 15/22 (2013.01); G10L 21/02 (2013.01); H04L 63/1416 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
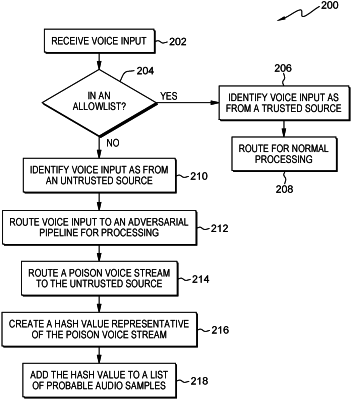
in response to receiving a voice input from a source, determining, using a predetermined filter including an allowlist, by one or more processors, that the voice input does not match any corresponding entry of the predetermined filter;
routing, by one or more processors, the voice input to an adversarial pipeline for processing by:
identifying an adversarial example of the voice input using a predetermined connectionist temporal classification (CTC) method;
generating a configurable distorted adversarial example using the adversarial example identified; and
in response to a user reply, injecting the configurable distorted adversarial example as noise into a voice stream of the user reply in real-time to alter the voice stream; and
routing, by one or more processors, the altered voice stream to the source.
|