| CPC H04L 63/1483 (2013.01) [H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 38 Claims |
|
1. A cybersecurity system for processing events to identify invalid ad traffic, the cybersecurity system comprising:
a plurality of rendering devices configured to perform the following steps:
collect event data in response to network traffic events;
generate network event metadata as a function of the event data; and
transmit the network event metadata;
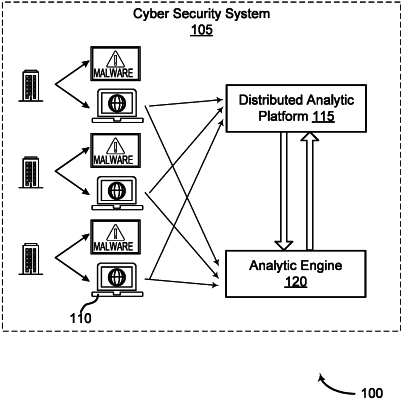
a plurality of sensors, wherein each of said plurality of sensors is coupled to at least one of said plurality of rendering devices, and wherein each of said plurality of sensors is configured to:
receive sensor data from at least one of the plurality of rendering devices;
process the sensor data to detect cyber events and generate cyber-event metadata; and
transmit the cyber-event metadata;
a distributed analytic platform coupled to each of the plurality of sensors via a network, the distributed analytic platform configured to perform the following steps:
receive the cyber-event metadata from the plurality of sensors;
process the cyber-event metadata using analytics to detect unwanted cyber activity;
generate analytic outputs as a function of detected unwanted cyber activity;
transmit the analytic outputs and associated behavioral metadata;
receive said cyber-events from said plurality of sensors;
process the cyber-events to form analytic workflows and distributed analytic platform messages, each of the distributed analytic platform messages associated with at least one of an alert, an update to a first analytic model, and cyber behavioral information, each of the analytic workflows associated with one or more logical segments, and including at least one analytic model; and
transmit the analytic workflows and the distributed analytic platform messages;
an analytic engine configured to perform the following steps:
receive the network event metadata from the plurality of rendering devices;
receive the analytic outputs from the distributed analytic platform;
correlate the network event metadata and the analytic outputs; and
identify at least one of the network traffic events as suspicious in response to the network event metadata and the analytic outputs having been correlated;
a plurality of scoring engines, each of the plurality of scoring engines configured to:
receive the analytic workflows from the distributed analytic platform,
receive the cyber events from at least one of the plurality of sensors,
process the cyber-event metadata using the analytic workflows to produce scoring engine messages, and
transmit the scoring engine messages;
a real time analytic engine, the real time analytic engine configured to:
receive the analytic workflows from the distributed analytic platform;
receive analytic workflow and event processing rules;
receive the scoring engine messages from the plurality of scoring engines;
receive the distributed analytic platform messages from the distributed analytic platform; and
process the scoring engine messages and the distributed analytic platform messages using the analytic workflows from the distributed analytic platform and the analytic workflow and event processing rules; and
wherein each of the one or more logical segments associate:
at least one of the first analytic model, a second analytic model, a third analytic model, a set of analytic models, and the analytic workflow,
one or more sources of inputs about activity within the one or more logical segments, and
a set of actions for mitigating an impact of anomalous activity occurring within the one or more logical segments;
wherein the analytic workflows comprise a Model Interchange Format document, wherein the Model Interchange Format document supports:
a composition of analytic models;
a segmentation of analytic models;
an ensemble of analytic models;
a composition of analytic models with rules;
a composition of analytic models with pre-processing and post-processing stages, wherein the pre-processing and post-processing stages include data transformations and data aggregations; and
the analytic workflows, each of the analytic workflows further comprising compositions of at least one of the analytic models, the rules, the data transformations, the data aggregations, the segmentations, and ensembles.
|