| CPC H04L 63/1425 (2013.01) [H04L 63/1416 (2013.01)] | 17 Claims |
|
1. A system for detecting anomalous access to system resources, the system comprising:
one or more processors; and
a non-transitory computer-readable storage medium storing instructions, which when executed by the one or more processors cause the one or more processors to:
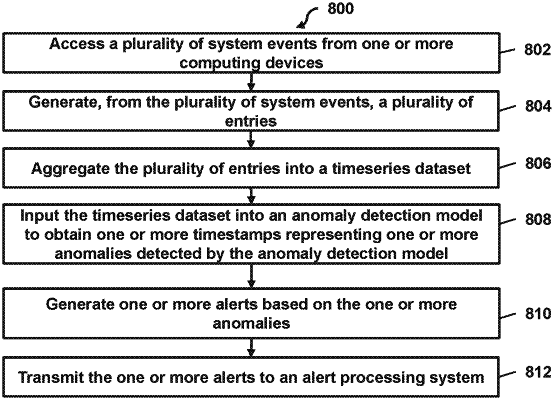
access a plurality of system events from one or more computing devices;
generate, from the plurality of system events, a plurality of entries, wherein each entry of the plurality of entries includes a corresponding timestamp indicating a time when a corresponding system event occurred, a corresponding user identifier indicating a user account within a computing environment associated with the corresponding system event, a corresponding location identifier indicating a location within the computing environment, and a corresponding action identifier indicating an action that the user account performed with respect to the location within the computing environment;
determine a plurality of equal time intervals for a time period associated with the plurality of entries;
for each time interval of the plurality of equal time intervals, transform a subset of the plurality of entries corresponding to a given equal time interval into a time series dataset based on unique combinations of a user identifier, a location identifier, and an action identifier, wherein the time series dataset comprises a corresponding aggregated value for each unique combination of the user identifier, the location identifier, and the action identifier;
input the time series dataset into an anomaly detection model;
receive, based on inputting the time series dataset comprising each corresponding aggregated value into the anomaly detection model, a plurality of timestamps representing a plurality of anomalies detected by the anomaly detection model and a plurality of probabilities corresponding to the plurality of timestamps, wherein each probability indicates a probability of an anomaly at the corresponding timestamp, and wherein the anomaly detection model is a machine learning model trained to detect anomalies within time series datasets that comprise the unique combinations of the user identifier, the location identifier, and the action identifier;
in response to receiving the plurality of anomalies from the anomaly detection model, compare each anomaly received from the anomaly detection model with an anomaly confidence threshold, wherein the anomaly confidence threshold indicates a threshold probability that a detected anomaly not a false positive;
remove, from the plurality of anomalies, one or more timestamps corresponding to those anomalies that do not meet the anomaly confidence threshold to generate an updated plurality of anomalies;
generate one or more alerts based on the updated plurality of anomalies; and
transmit the one or more alerts to an alert processing system.
|