| CPC H04L 63/105 (2013.01) [G06F 9/4887 (2013.01); G06F 9/5088 (2013.01); G06F 16/13 (2019.01); G06F 16/134 (2019.01); G06F 16/162 (2019.01); G06F 16/21 (2019.01); G06F 16/2228 (2019.01); G06F 16/2272 (2019.01); G06F 16/901 (2019.01); G06F 16/951 (2019.01); G06F 16/955 (2019.01); G06F 16/9537 (2019.01); G06F 16/986 (2019.01); G06F 21/6218 (2013.01); G06Q 20/145 (2013.01); H04L 12/1435 (2013.01); H04L 63/10 (2013.01); H04L 67/1097 (2013.01)] | 20 Claims |
|
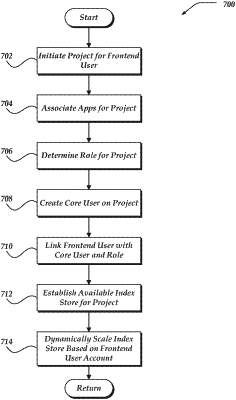
1. A computer-implemented method, comprising;
receiving a request for a first user to access an indexed data store associated with a project, wherein the request is based on an invitation received from a second user, and wherein at least some events in a set of events in the indexed data store comprise a portion of raw machine data associated with a timestamp;
determining that the second user is assigned a first role included in one or more roles that enable access to the indexed data store, wherein the first role is associated with a set of permissions for accessing the indexed data store;
assigning at least the first role to the first user based on the second user being assigned the first role;
determining, based on the set of permissions associated with the first role, a set of operations that the first user has permission to perform on the set of events stored in the indexed data store; and
allowing the first user to perform an operation included in the set of operations.
|