| CPC H04L 63/0281 (2013.01) [G06F 21/55 (2013.01); G06F 21/554 (2013.01); G06F 21/6281 (2013.01); G06N 20/00 (2019.01); H04L 63/02 (2013.01); H04L 63/04 (2013.01); H04L 63/0807 (2013.01); H04L 63/0876 (2013.01); H04L 63/1425 (2013.01); H04L 63/1458 (2013.01); H04L 63/1491 (2013.01)] | 18 Claims |
|
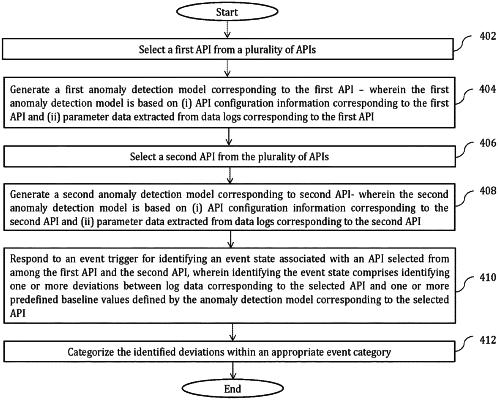
1. A non-transitory processor-readable medium storing code representing instructions to be executed by a processor, the instructions comprising code to cause the processor to:
receive an event trigger to analyze traffic parameter data associated with network traffic of an Application Programming Interface (API);
identify the API as associated with an API class from a plurality of API classes;
identify, in response to the event trigger, an anomaly detection model from a plurality of anomaly detection models and associated with the API class, each anomaly detection model from the plurality of anomaly detection models being associated with a different API class from the plurality of API classes;
analyze, using the anomaly detection model and in response to the event trigger, the traffic parameter data to identify deviations between the traffic parameter data and a traffic parameter baseline value associated with the API; and
restrict network traffic associated with the API when the deviations meet a criterion.
|