| CPC H04L 43/18 (2013.01) [H04L 63/08 (2013.01); H04L 67/02 (2013.01)] | 18 Claims |
|
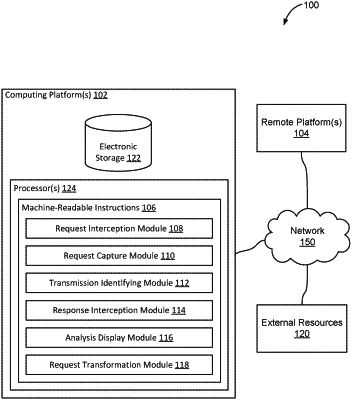
1. A system configured for analyzing authentication and authorization requirements in an identity infrastructure, the system comprising:
one or more hardware processors configured by machine-readable instructions to:
intercept, at a server, a first request to access an application in the identity infrastructure, wherein the first request is received from a first user device;
transmit, from the server, one or more of the first request and a modified version of the first request to the application;
intercept, at the server, a response from the application, based at least in part on the transmission;
display, via at least one interface, an analysis of one or more of the first request, the modified version of the first request, and the response, wherein the analysis comprises determining at least one of: requirements for application authentication and authorization, one or more identity protocols utilized by the application, one or more identity techniques utilized by the application, whether application meets predetermined compliance standards, and whether any user-defined security requirements have been implemented; and
capture a second request to access the application, wherein the second request comprises the modified version of the first request and includes one or more identity dependencies received from an identity and access management (IAM) system;
wherein the transmission comprises transmitting the second request to the application; and
wherein intercepting the response comprises intercepting the response from one of the IAM system or the application.
|