| CPC G06Q 20/405 (2013.01) [G06Q 20/34 (2013.01); G06Q 20/409 (2013.01)] | 20 Claims |
|
1. A system for implementing a hierarchy of rule-based security authentication modes, the system comprising:
a memory component that stores one or more user authentication profiles; and
an authentication rule selection engine including a computer processor, coupled to the memory component, the computer processor programmed to perform operations, including
receiving from a user, via the computer processor, a selection of a plurality of authentication profiles, the authentication profiles, including one or more security authentication modes based on one or more attributes for a potential user transaction request;
utilizing artificial intelligence, machine learning and neural networks, via the computer processor, to learn the user's habits and patterns;
providing, via the computer processor, feedback to the user, including one or more suggestions to update the user selection of the plurality of authentication profiles based on the learned user's habits and patterns;
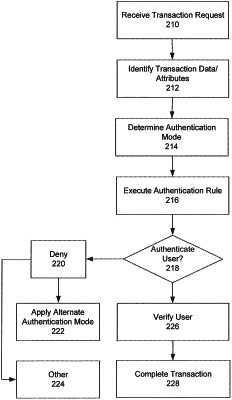
receiving, via a transaction gateway, a transaction request associated with an instrument from the user at a transaction initiation system;
determining, via the computer processor, a plurality of transaction attributes for the transaction request including a transaction location, a transaction recipient, a transaction type, a transaction amount, and a wifi network for the transaction request;
determining, via the computer processor, a proper security authorization mode for the transaction request based on the plurality of one or more transaction attributes;
executing, via the computer processor, an authentication rule for the transaction request;
transmitting, via a communication network, an authentication request to the user;
requiring, via a user-selected security authorization mode, an authorization input from the user responsive to the authentication request;
upon receiving a correct authentication input via an improper security authorization mode:
automatically informing the user of the correct authentication input via one or more modes of electronic communication;
transmitting, to an electronic communication account of the user, a presentation of an option to reset the correct authentication input;
activating an additional security authentication mode requiring biometric input information; and
applying an additional authentication request;
upon receiving the correct authentication input via the proper security authorization mode, verifying the user and proceeding with the transaction request; and
upon receiving an improper authentication input:
automatically informing the user of the improper authentication input via the one or more modes of electronic communication;
activating the additional security authentication mode requiring the biometric input information; and
applying the additional authentication request.
|