| CPC G06F 9/45541 (2013.01) [G06F 9/45558 (2013.01); G06F 9/5011 (2013.01); G06F 9/5077 (2013.01); G06F 9/5044 (2013.01); G06F 9/5072 (2013.01); G06F 2009/4557 (2013.01); G06F 2209/508 (2013.01)] | 20 Claims |
|
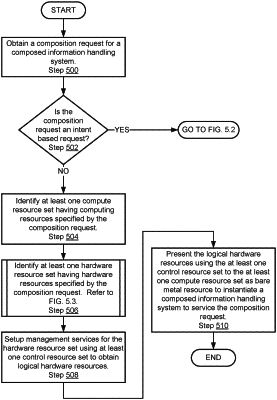
13. A method for dynamically instantiating composed information handling systems (IHSs), comprising:
obtaining, from a user, a composition request (CR) for a composed IHS of the composed IHSs;
making a determination that the composition request is an intent based request, wherein the intent based request specifies a set of predetermined characteristics that the user wants to have in the composed IHS without specifying makes, types, and quantities of computing resources to be allocated to the composed IHS,
wherein the set of predetermined characteristics comprises a first characteristic that the composed IHS executes a workload, a second characteristic that the composed IHS provides a service, and a third characteristic that the composed IHS employs a security model,
wherein, based on a lookup table, a computer processor (CP) heuristically converts the intent based request into required computing resources, wherein the required computing resources specifies makes, types, and quantities of computing resources required to be allocated to the composed IHS to satisfy the set of predetermined characteristics;
in response to the determination:
identifying, based on the required computing resources, a physical compute resource set of a first IHS,
wherein, based on the first identification, the CP sends a first request to a first system control processor of the first IHS to allocate the physical compute resource set for the composed IHS;
identifying, based on the required computing resources, a physical hardware resource set of a second IHS,
wherein, based on the second identification, the CP sends a second request to a second system control processor of the second IHS to allocate the physical hardware resource set for the composed IHS;
identifying, based on the required computing resources, a physical control resource set of a third IHS,
wherein, based on the third identification, the CP sends a third request to a third system control processor of the third IHS to allocate the physical control resource set for the composed IHS; and
instantiating the composed IHS based on the physical compute resource set, the physical hardware resource set, and the physical control resource set, wherein the physical control resource set supports an in-band connection to assist the composed IHS for servicing the user and an out-of-band connection to manage the composed IHS.
|