| CPC G06F 21/6245 (2013.01) [G06F 16/2379 (2019.01); G06F 16/27 (2019.01); G06F 21/602 (2013.01); G06K 7/1417 (2013.01); G06K 19/06037 (2013.01); H04L 9/0643 (2013.01); H04L 9/3231 (2013.01)] | 17 Claims |
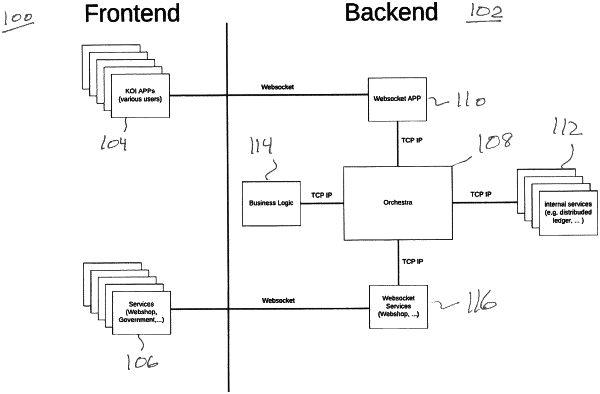
|
1. A computer-implemented method for selectively verifying personal data, the method comprising:
receiving, by an identity application of a client device, personal data of a user;
computing, via a cryptographic hash function, one or more cryptographic hashes from elements of the personal data;
storing the cryptographic hashes, an internal identifier and a timestamp as an entry in a distributed database,
wherein the internal identifier is unique within the distributed database;
receiving a user request from the user;
selecting one or more of the elements of personal data for verification;
requesting verification of the selected elements of personal data, wherein the verification request further comprises:
reading, by the client device, a machine-readable representation of the verification request, wherein the machine-readable representation may include a quick response code;
independently creating a second hash of the selected one or more elements; and
comparing the second hash to the computed cryptographic hash;
determining an authorization indication in response to the verification request;
when the authorization indication indicates that the verification request has been allowed, and the selected elements of personal data are accessible, verifying the selected elements of personal data using cryptographic hashes from the entry in the distributed databases;
maintaining, by a distribution service, a list of approved providers for the user, wherein each provider on the list is authorized to maintain at least one element of the personal data;
receiving, by the distribution service and from the client device, a change to the personal data; and
sending an update corresponding to the change to each provider on the list of approved providers.
|