| CPC G06F 21/6227 (2013.01) [G06F 16/906 (2019.01); G06F 16/953 (2019.01); G06F 16/986 (2019.01); G06N 20/00 (2019.01)] | 20 Claims |
|
1. A method comprising:
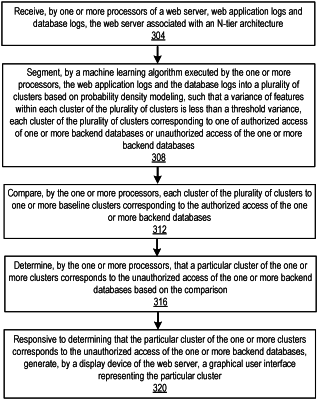
receiving, by one or more processors of a web server, web application logs and database logs, the web server associated with an N-tier architecture;
segmenting, by a machine learning algorithm executed by the one or more processors, the web application logs and the database logs into a plurality of clusters based on probability density modeling, such that a variance of features within each cluster of the plurality of clusters is less than a threshold variance, each cluster of the plurality of clusters corresponding to one of authorized access of one or more backend databases or unauthorized access of the one or more backend databases;
comparing, by the one or more processors, each cluster of the plurality of clusters to one or more baseline clusters corresponding to the authorized access of the one or more backend databases;
determining, by the one or more processors, that a particular cluster of the one or more clusters corresponds to the unauthorized access of the one or more backend databases based on the comparison; and
responsive to determining that the particular cluster of the one or more clusters corresponds to the unauthorized access of the one or more backend databases, generating, by a display device of the web server, a graphical user interface representing the particular cluster.
|