| CPC G06F 21/577 (2013.01) [G06F 2221/034 (2013.01); G06F 2221/2101 (2013.01)] | 17 Claims |
|
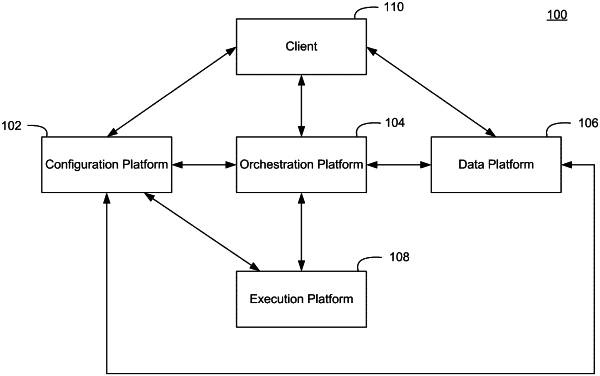
1. A system for managing breach simulation results generated in a networked production environment, the networked production environment comprising hardware components coupled in a network, the system comprising:
a memory device having executable instructions stored therein; and
a processing device, in response to the executable instructions, configured to:
receive a set of simulation results of a breach scenario workflow from a simulation orchestrator which have been processed by a results analyzer subsystem, wherein the breach scenario workflow includes one or more malicious actions representing a scenario found successful from an attacker point of view that violates a security policy of the networked production environment;
retrieve a stored snapshot of known breaches in the networked production environment with the simulation results, the snapshot comprising an in-memory graph including a plurality of nodes and edges, the nodes in the in-memory graph representing simulator nodes between which a breach simulation was executed, and the edges in the in-memory graph representing simulation results of specific breach scenarios between the simulator nodes;
determine whether any of the simulation results represent a new breach scenario by searching the in-memory graph for a breach scenario matching the simulation results and, in response to determining that no such breach scenario is found, updating the in-memory graph to include any simulation results so determined to be a new breach scenario; and determine whether any of the simulation results represent a fixed breach scenario by searching the in-memory graph for a breach scenario matching the simulation results and, in response to determining that the simulation results show the breach was fixed, concluding the breach scenario by updating the in-memory graph to reflect the breach scenario was fixed.
|