| CPC G06F 21/577 (2013.01) [G06F 21/55 (2013.01); G06F 2221/034 (2013.01)] | 15 Claims |
|
1. A system for security risk identification in a software application, the system comprising:
one or more hardware processor;
one or more memory in the one or more hardware processor, the one or more memory comprising:
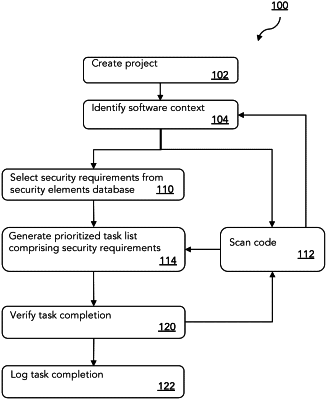
a security knowledge database comprising a plurality of security elements, each security element comprising an identification of a security risk and a recommended remediation task for remediating the security risk;
a security element selection module for automatically selecting a customized set of security requirements for the software application from the plurality of security elements in the security knowledge database and automatically retrieving the customized set of security requirements from the security knowledge database, the customized set of security requirements includes security elements from the plurality of security elements that are relevant to software context of the software application, the software context comprising characteristics of the software environment pertaining to coding and running of the software application;
an automated code scanner for automatically identifying one or more instances of code vulnerability in software application code of the software application, the code scanner having a tool-specific mapping such that each of the one or more instances of code vulnerability identified by the code scanner is associated with and mapped to at least one of the security requirements for the software application together with the ability of the code scanner to identify a security risk associated with the at least one mapped security requirement;
a prioritization engine for prioritizing the customized set of security requirements by identifying security requirements in the customized set of security requirements that are ineffectively identified by the code scanner, that are not associated with the instances of code vulnerabilities identified by the code scanner mapping, and for which the automated code scanner is incapable of verifying a compliance state, the prioritizing generates a prioritized list of the customized set of security requirements based on the security risk of each of the security requirements in the customized set of security requirements by assigning higher priorities to security requirements with higher security risks; and
a task list generator for dynamically generating and automatically updating a task list for the software application, the task list comprising the recommended remediation tasks in the prioritized list of the customized set of security requirements wherein the task list is prioritized according to the priorities assigned in the prioritized list.
|