| CPC G06F 21/565 (2013.01) [G06F 8/71 (2013.01); G06N 7/01 (2023.01); G06N 20/00 (2019.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
1. A method comprising:
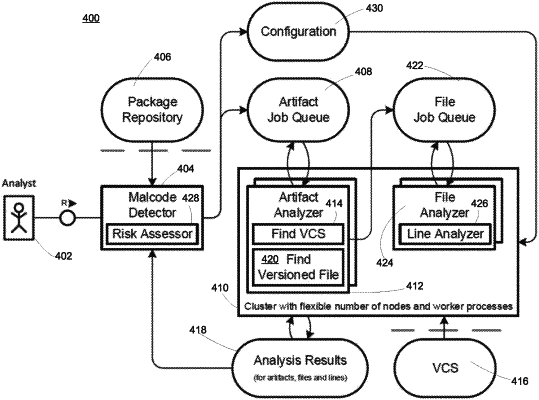
receiving an artifact comprising a set of software code files, wherein each software code file in the set of software code files comprises a plurality of source code lines in a programming language;
determining, for each software code file in the set of software code files of the artifact, whether a file under analysis in the set of software code files corresponds to a versioned file that is in a Version Control System (VCS), wherein the versioned file comprises a commit information;
in response to determining the file under analysis does correspond to the versioned file, determining, for each source code line in the plurality of source code lines of the file under analysis, whether a source code line under analysis is in the commit information of the versioned file by:
issuing a query to the VCS based on the source code line;
receiving a response to the query comprising the commit information of the versioned file from the VCS;
reading the commit information line by line;
detecting that the source code line under analysis is not in the commit information of the versioned file in the VCS;
generating a first malicious probability for the line under analysis based on the file under analysis and the line under analysis;
in response to determining the file under analysis does not correspond to the versioned file in the VCS, generating a second malicious probability for each source code line of the file under analysis based on the file under analysis and each source code line of the file under analysis; and
communicating each file under analysis, each source code line under analysis, and one of the first malicious probability and the second malicious probability corresponding to each source code line under analysis of each file under analysis for review.
|