| CPC G06F 21/54 (2013.01) [G06F 21/566 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, suppresses false positive indications of return-oriented programming attacks by performing the steps of:
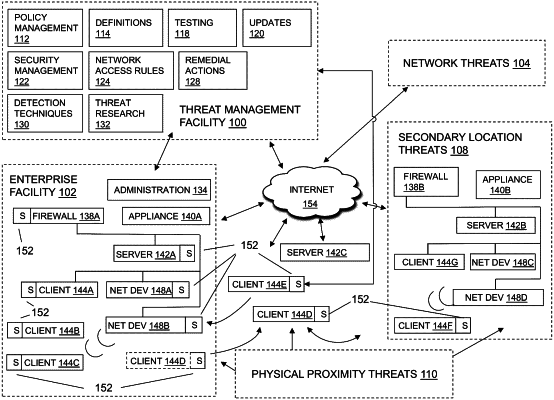
deploying a security measure to detect control-flow integrity compromises indicative of a return-oriented programming (ROP) exploit on a computing device;
receiving a report of a possible ROP exploit from the security measure, the report including contextual information for the possible ROP exploit, wherein the contextual information further includes path information for one or more files associated with the possible ROP exploit and branch information for one or more processes associated with the possible ROP exploit;
normalizing the report to isolate machine-specific variations in the path information and the branch information;
hashing the normalized report to provide a hashed report;
pre-filtering the hashed report with a filter to determine if the report belongs to a collection of known false-positive reports; and
in response to determining, based on applying the filter to the hashed report, that the report of the possible ROP exploit does not belong to a collection of known false-positive reports, responding to the report with a remediation for the possible ROP exploit.
|