| CPC G06F 16/906 (2019.01) [G06F 3/0482 (2013.01); G06F 16/125 (2019.01); G06F 16/907 (2019.01); G06F 16/9038 (2019.01); H04L 63/105 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
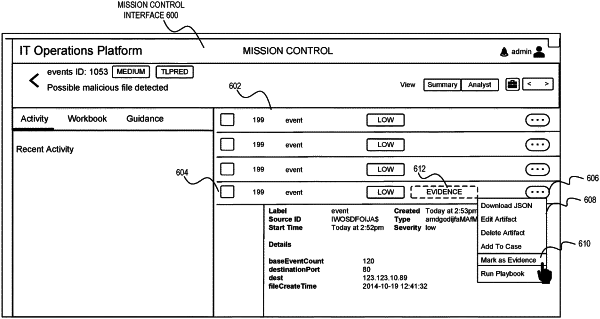
1. A computer-implemented method performed by an information technology (IT) operations platform, the method comprising:
identifying a first data object within the IT operations platform as evidence relevant to an incident in an IT environment; and
in response to identifying the first data object as evidence:
storing metadata in association with the first data object that identifies the first data object as evidence within the IT operations platform;
modifying permissions associated with the first data object;
automatically executing a search using the metadata associated with the first data object to identify a second data object within the IT operations platform that is related to the first data object but is not identified as evidence relevant to the incident;
identifying the second data object as evidence relevant to the incident; and
modifying permissions associated with the second data object to restrict an ability for the second data object to be modified or deleted.
|