| CPC G06F 16/2365 (2019.01) | 18 Claims |
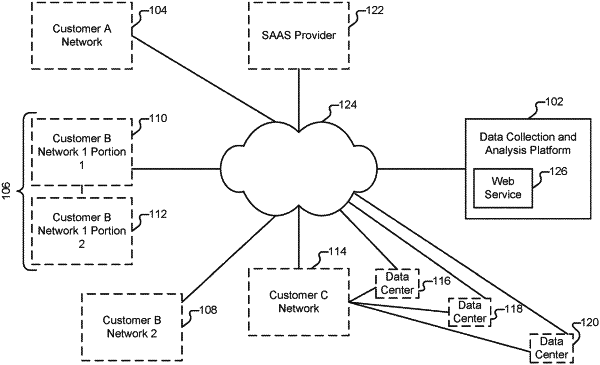
|
1. A computer-implemented method comprising:
identifying a first plurality of log entries received over a predefined period of time;
categorizing each log entry from the first plurality of log entries, into a category from a plurality of categories; based on a signature of the log entry, wherein the signature is based on a printf statement configured to generate log entries associated with the signature;
creating a baseline based on a number of log entries in each category, the baseline being a representative quantity received over the predefined period of time;
identifying a second plurality of log entries;
categorizing each log entry from the second plurality of log entries;
detecting an anomaly in one category from the plurality of categories based on a count of log entries from the second plurality of log entries in the category deviating from the count of log entries from the first plurality of log entries in the category by a predetermined threshold; and
causing presentation on a user interface (UI) of the detected anomaly; wherein causing presentation on a user interface (UI) of the detected anomaly further comprises:
presenting in the UI log entries with a signature not present in the baseline with a label indicating the log entries that are new; and
presenting logs missing from the baseline with a label of gone.
|