| CPC H04L 63/1458 (2013.01) [H04L 63/1416 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
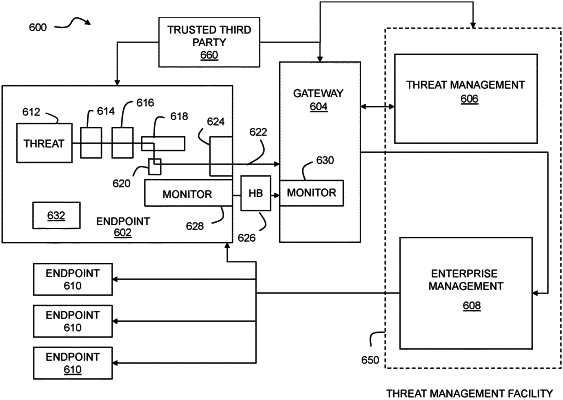
1. A computer program product for protecting against distributed denial of service attacks from an enterprise network, the computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, performs the steps of:
detecting a potential trigger event on an endpoint in the enterprise network for a distributed denial of service attack;
in response to detecting the potential trigger event, monitoring outbound traffic from the endpoint for an increase in network traffic from the endpoint directed to a known, good reputation network address over a predetermined time;
in response to the potential trigger event followed by the increase in network traffic over the predetermined time, identifying the endpoint as having a compromised state in which the endpoint serves as a distributed denial of service bot for the distributed denial of service attack; and
preventing all network traffic from the endpoint to the known, good reputation network address until the compromised state is remediated.
|