| CPC H04L 63/1441 (2013.01) [G06F 3/0486 (2013.01); G06F 3/04842 (2013.01); G06F 16/2455 (2019.01); G06F 18/23 (2023.01); G06F 18/232 (2023.01); G06F 21/36 (2013.01); G06F 21/554 (2013.01); G06F 21/556 (2013.01); G06F 40/40 (2020.01); G06N 20/00 (2019.01); G06N 20/10 (2019.01); G06V 30/10 (2022.01); H04L 41/22 (2013.01); H04L 43/045 (2013.01); H04L 51/212 (2022.05); H04L 51/224 (2022.05); H04L 51/42 (2022.05); H04L 63/0209 (2013.01); H04L 63/0428 (2013.01); H04L 63/101 (2013.01); H04L 63/14 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1483 (2013.01); H04L 63/20 (2013.01); G06N 20/20 (2019.01)] | 20 Claims |
|
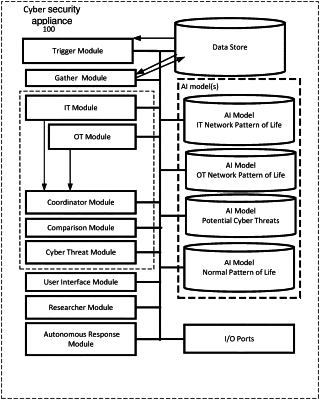
1. A cyber security appliance, comprising:
a processor and a memory, which further comprise:
an operational technology module configured to receive data on an operational technology network from i) a set of probes, ii) by passive traffic ingestion through a location within the network, and iii) any combination of both, where the operational technology module is also configured to reference
i) one or more machine-learning models, using machine-learning and artificial intelligence (AI) algorithms, that are trained on a normal pattern of life of users of the operational technology network,
ii) one or more machine-learning models, using machine-learning and AI algorithms, that are trained on a normal pattern of life of devices in the operational technology network, and
iii) one or more machine-learning models, using machine-learning and AI algorithms, that are trained on a normal pattern of life of controllers in the operational technology network; and
a comparator module configured to cooperate with the operational technology module to compare the received data on the operational technology network to the normal pattern of life of any of the users, devices, and controllers to detect anomalies in the normal pattern of life for these entities in order to detect a cyber threat; and
an autonomous response module configured to respond to counter the cyber threat, and a user interface to program the autonomous response module.
|