| CPC H04L 63/101 (2013.01) [H04L 63/0807 (2013.01); H04L 63/0884 (2013.01); H04L 63/1425 (2013.01)] | 20 Claims |
|
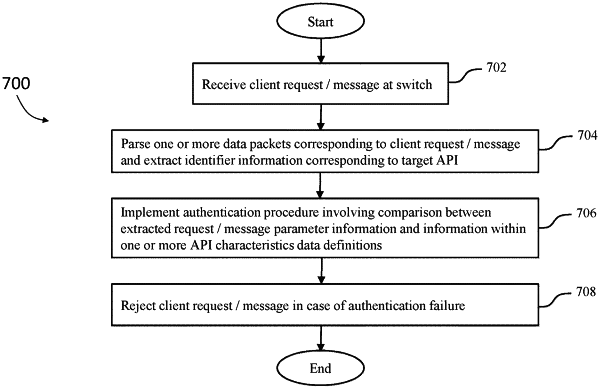
1. A method, comprising:
receiving, at an access control server, a server resource request message from a client, the server resource request message requesting information from a server resource;
extracting server resource request message data from the server resource request message;
sending the server resource request message data to a security server such that the security server, in response to receiving the server resource request message data, analyzes the server resource request message data to identify whether there is an error, anomaly, or indicator of compromise associated with the server resource request message;
routing, prior to receiving a message from the security server indicating that there is an error, anomaly, or indicator of compromise associated with the server resource request message, the server resource request message and one or more additional server resource request messages subsequently received from the client to a resource server implementing the server resource; and
in response to receiving the message from the security server indicating that there is an error, anomaly, or indicator of compromise associated with the server resource request message, blocking server resource request messages subsequently received from the client from being sent to the resource server and responses from the resource server subsequently being sent to the client from being sent to the client.
|