| CPC H04L 41/145 (2013.01) [H04L 41/12 (2013.01); H04L 41/147 (2013.01); H04L 41/5067 (2013.01); H04L 43/045 (2013.01); H04L 43/06 (2013.01); H04L 43/0817 (2013.01); H04L 43/55 (2022.05)] | 20 Claims |
|
1. A computer-implemented method comprising:
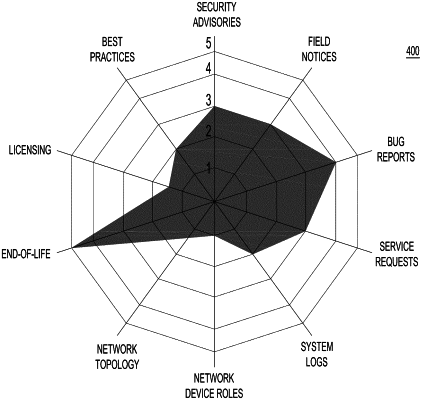
obtaining customer data for a first network, wherein the customer data indicates a role of one or more network devices in the first network and a plurality of risk reports corresponding to the one or more network devices, wherein each risk report is associated with one of a plurality of dimensions of risk that include a recommended configuration of hardware or software of the first network;
generating a network profile image by processing the plurality of risk reports;
generating a synthetic network profile image from the network profile image, wherein the synthetic network profile image does not include the customer data;
evaluating a second network using the synthetic network profile image using a second network profile image generated by processing a second plurality of risk reports corresponding to a second plurality of dimensions of risk of the second network by comparing the synthetic network profile image to the second network profile image; and
identifying differences between the first network and the second network based on a comparison of the plurality of dimensions of risk to the second plurality of dimensions of risk.
|