| CPC G06Q 20/3829 (2013.01) [G06Q 20/00 (2013.01); G06Q 20/382 (2013.01); G06Q 20/3823 (2013.01); H04L 63/083 (2013.01); H04L 63/062 (2013.01); H04L 2463/061 (2013.01)] | 13 Claims |
|
1. A method for generating cryptograms in a webservice environment, comprising:
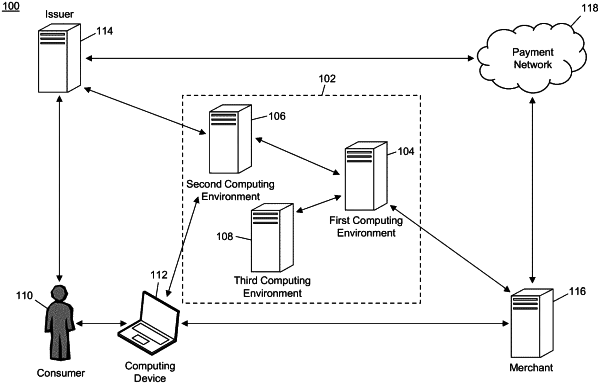
receiving, by a receiving device of a second computing device of a computing system, a data request from a first computing device of the computing system, said data request includes at least an account identifier;
forwarding, by the receiving device of the second computing device to a communication module of the second computing device, the data request;
forwarding, by the communication module of the second computing device and to a querying module of the second computing device, the data request;
identifying, by the querying module of the second computing device of the computing system, an account profile using the account identifier included in the data request and a session key associated with the account profile;
forwarding, by the querying module of the second computing device and to the communication module of the second computing device, the account profile and the session key;
forwarding, by the communication module of the second computing device and to the transmitting device of the second computing device, the account profile and the session key;
transmitting, from the transmitting device of the second computing device, to a receiving device of the first computing device of the computing system, at least the account profile and the session key;
transmitting, by a transmitting device of the first computing device of the computing system, to a third computing device of the computing system, a cryptogram request that includes at least the account profile and one of: the session key or a secondary key derived from the session key;
generating, by a generation module of the third computing device of the computing system, a cryptogram using at least the account profile and one of the session key or the secondary key;
transmitting, by a transmitting device of the third computing device of the computing system, the cryptogram to the first computing device of the computing system, whereat the cryptogram and the transaction identifier are associated by generation of a data message including the cryptogram and the transaction identifier; and
transmitting, by the transmitting device of the first computing device of the computing system, to a merchant computing device external to the computing system and via a secure communication protocol, a second data signal comprising the data message.
|