| CPC G06F 21/85 (2013.01) [G06F 9/45533 (2013.01); G06F 13/4221 (2013.01); G06F 21/31 (2013.01); G06F 21/602 (2013.01); H04L 9/088 (2013.01); H04L 9/0897 (2013.01); H04L 9/3278 (2013.01); H04L 63/20 (2013.01); G06F 2213/0026 (2013.01)] | 23 Claims |
|
1. An integrated circuit device comprising:
an I/O port;
a host interface configured to be connected to a host, wherein the host interface comprises a Peripheral Component Interface express (PCIe) interface;
a data processing pipeline within the integrated circuit device coupled to the I/O port and to the PCIe interface to process and forward data between the I/O port and the PCIe interface; and
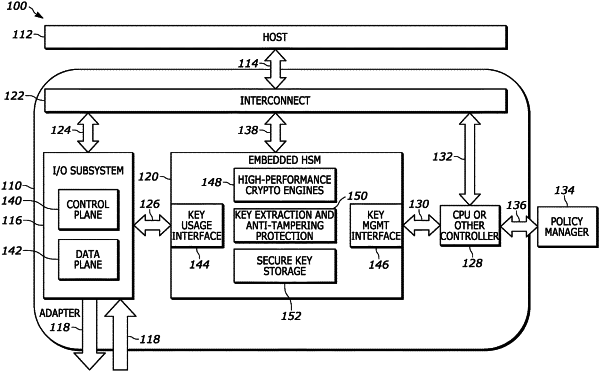
a hardware security module (HSM) within the integrated circuit device coupled to the PCIe interface and to the data processing pipeline, the HSM comprising a crypto engine configured to encrypt and decrypt data of the data processing pipeline, and a secure key storage coupled to the crypto engine and configured to contain encryption keys for use in encrypting and decrypting packets, wherein the secure key storage is configured to contain keys that are encrypted by the HSM and that are accessible through the HSM;
wherein the HSM further comprises a key usage interface coupled to the data processing pipeline, wherein the key usage interface is configured to be accessed by key users of the host through the PCIe interface to encrypt and decrypt data in the data processing pipeline and wherein the key usage interface is configured to authenticate and identify the key users based on functions of the PCIe interface that are invoked by the key users to access the data processing pipeline; and
wherein the key users are virtual machines and wherein the functions are virtual functions of the PCIe interface and wherein the virtual machines are authenticated based on presence on the PCIe interface and identified based on virtual functions invoked by the respective virtual machine.
|