| CPC G06F 21/6245 (2013.01) [G06F 21/602 (2013.01); G06F 21/62 (2013.01); G06F 21/6254 (2013.01); H04L 9/008 (2013.01); H04L 9/0643 (2013.01); H04L 9/0869 (2013.01); H04L 9/14 (2013.01); G06F 2221/2107 (2013.01)] | 16 Claims |
|
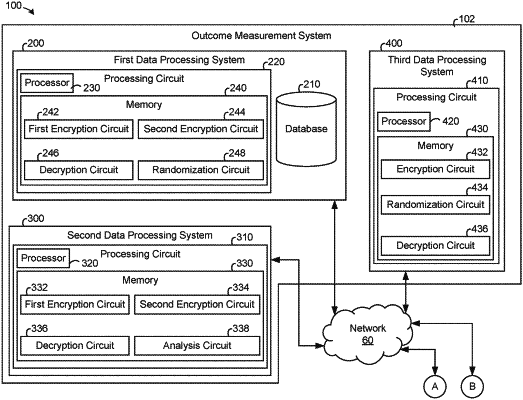
1. A method, comprising:
receiving, at a first computing system, encrypted identifiers and encrypted values;
performing, by the first computing system, a concealing operation on the encrypted identifiers to produce concealed encrypted identifiers, wherein the concealing operation conceals the encrypted identifiers from the first computing system and a second computing system but enables matching between the concealed encrypted identifiers;
decrypting, by the second computing system, the concealed encrypted identifiers to produce concealed identifiers;
performing, by the second computing system, an aggregation operation using the concealed identifiers and the encrypted values to produce an encrypted aggregate value without accessing personal information associated with the encrypted values;
decrypting, by a third computing system, the encrypted aggregate value to produce an aggregate value;
cooperatively generating by the first computing system and the second computing system a first encryption key;
generating by the first computing system a second encryption key associated with the first encryption key and a third encryption key;
generating by the second computing system a first decryption key associated with the first encryption key; and
generating by the third computing system a second decryption key and a fourth encryption key.
|