| CPC G06F 21/6218 (2013.01) [G06F 9/45558 (2013.01); G06F 12/1009 (2013.01); G06F 12/1475 (2013.01); G06F 21/52 (2013.01); G06F 21/604 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45595 (2013.01)] | 20 Claims |
|
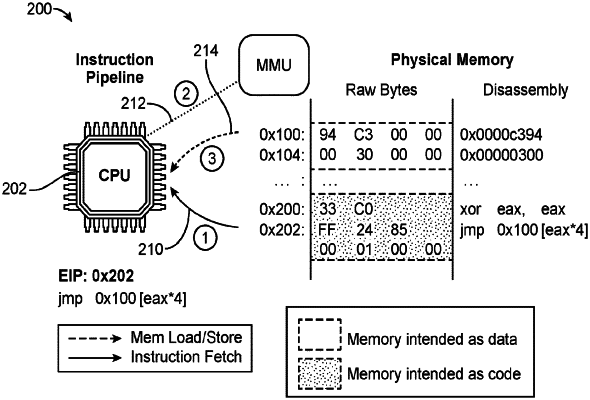
1. A method comprising:
determining, by a processor-based device, whether an operation to access a memory location containing executable code representative of a decodable instruction executable on the processor-based device comprises one of a plurality of general-purpose memory access operations that do not cause execution of the decodable instruction on the processor-based device; and
performing, by the processor-based device, the operation to access the memory location to read from the memory location the executable code representative of the decodable instruction; and
overwriting the memory location by the processor-based device, in response to a determination that the operation to access the memory location containing the executable code representative of a decodable instruction is a general-purpose memory access operation from the plurality of general purpose memory access operations, with a new content different than the executable code after reading the executable code from the memory location.
|