| CPC G06F 21/62 (2013.01) [G06F 21/604 (2013.01); H04L 9/0861 (2013.01); H04L 63/0428 (2013.01); H04L 63/083 (2013.01); H04L 63/0876 (2013.01); H04L 63/10 (2013.01); H04L 63/20 (2013.01); H04L 2463/082 (2013.01)] | 20 Claims |
|
1. A method, comprising:
requesting, via an electronic computing device, access to a third party system;
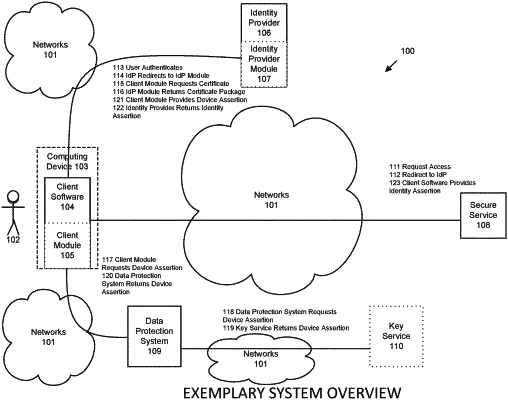
receiving, via the electronic computing device and from the third party system, a request for a cryptographic assertion, wherein the cryptographic assertion verifies to the third party system that a data protection system is operational on the electronic computing device prior to accessing the third party system;
extracting, via the electronic computing device, a common name from a certificate associated with the third party system;
generating, via the electronic computing device, a nonce corresponding to the request for the cryptographic assertion;
generating, via the electronic computing device, an encrypted client data package comprising a device identifier for the electronic computing device and the nonce;
sending, via the electronic computing device, an encrypted package to the data protection system for verification that the data protection system is operational, wherein the encrypted package comprises the common name and the encrypted client data package;
validating, via the data protection system, the request for the cryptographic assertion, wherein validating the request comprises:
determining, via the data protection system, that the request is not a replay of a previous request based at least in part on the nonce; and
comparing, via the data protection system, the device identifier to a known fingerprint hash for the electronic computing device;
in response to validating the request, sending, via the data protection system, the common name and the encrypted client data package to a key service; and
receiving, via the data protection system, a signed device assertion from the key service.
|