| CPC G06F 21/604 (2013.01) [G06F 21/31 (2013.01); G06F 21/57 (2013.01); G06F 21/602 (2013.01); G06F 21/6218 (2013.01); H04L 9/0643 (2013.01); H04L 9/3213 (2013.01); H04L 9/3297 (2013.01); H04L 63/08 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2141 (2013.01); H04L 9/50 (2022.05)] | 20 Claims |
|
1. A computer-implemented cryptographic method for generating a temporal permission for accessing encrypted data by a cryptographic token, the method comprising:
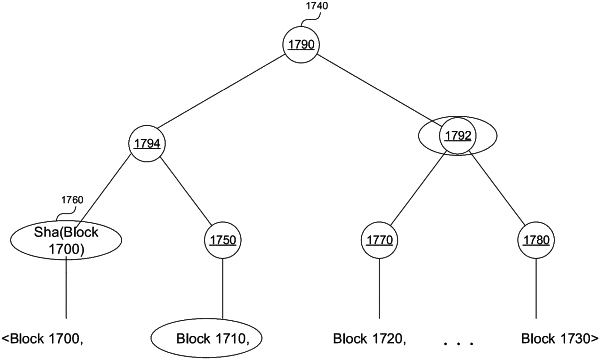
generating, by a computer system, a plurality of blocks for a block chain controlling access to the encrypted data;
generating a cryptographic hash tree comprising a plurality of endpoints representing the plurality of blocks,
wherein only a subset of the plurality of blocks are members of the cryptographic hash tree,
wherein each block of the plurality of blocks comprises a wall clock field, a sequence clock field, and a root of the cryptographic hash tree, and
wherein the wall clock field is indicated by a clock of a server storing the block chain;
generating the temporal permission for the cryptographic token based on a particular sequence clock field of the plurality of blocks;
incorporating the temporal permission into the cryptographic token to prevent access to the encrypted data by the cryptographic token after a particular time specified by the particular sequence clock field has passed; and
sending the cryptographic token to a user device for use in accessing the encrypted data.
|