| CPC H04W 12/06 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0838 (2013.01); H04L 9/0861 (2013.01); H04L 9/0894 (2013.01); H04L 9/3236 (2013.01); H04L 9/3247 (2013.01); H04L 63/0442 (2013.01); H04W 12/03 (2021.01); H04W 12/40 (2021.01); H04L 2209/80 (2013.01)] | 19 Claims |
|
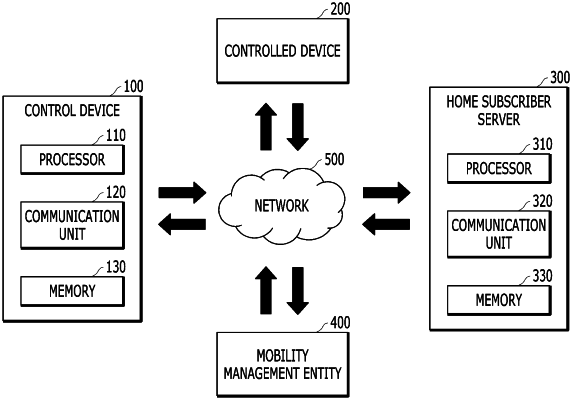
1. A computer program stored in a non-transitory computer readable storage medium, in which the computer program includes commands which cause a processor of a control device to execute steps below, the steps comprising:
acquiring International Mobile Station Identity (IMSI) related to a Subscriber Identity Module (SIM) and location information of a controlled device from the controlled device;
calculating a hash value obtained by hashing the IMSI by using a hash function;
generating first signature data in which the hash value and the location information are encrypted with a private key of the control device by using an asymmetric key algorithm;
generating first encryption data obtained by encrypting the first signature data with a public key of a home subscriber server by using the asymmetric key algorithm; and
transmitting a connection request message including the first encryption data to the home subscriber server,
wherein the steps further comprises:
receiving a connection response message including second encryption data from the home subscriber server, when the home subscriber server determines a connection acceptance for the connection request message;
extracting a random value, a first authentication token and a Temporary Mobile Subscriber Identity (TMSI) from the second encryption data; and
transmitting the random value, the first authentication token, and the first TMSI to the controlled device by using a wired secure channel.
|