| CPC H04L 63/1466 (2013.01) [G06F 16/986 (2019.01); H04L 51/18 (2013.01); H04L 63/0281 (2013.01); H04L 67/02 (2013.01); H04L 67/56 (2022.05)] | 20 Claims |
|
1. A method comprising:
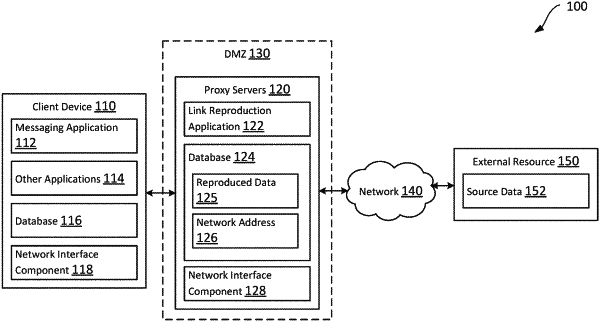
receiving, by a proxy server, an incoming electronic communication;
identifying a link within the incoming electronic communication;
analyzing a domain associated with the link, wherein the analyzing includes a domain reputation check of the domain;
implementing a security measure at the proxy server that protects an internal system designated for receipt of the incoming electronic communication from malicious or potentially malicious communications, wherein the security measure is based in part on the domain analyzed;
converting, based on the security measure, dynamic data accessible via the link to static data available on the proxy server; and
reproducing, at the internal system, the link with a mirrored link that enables link processing of the static data in place of the dynamic data.
|