| CPC H04L 63/1425 (2013.01) [G06F 16/2255 (2019.01)] | 15 Claims |
|
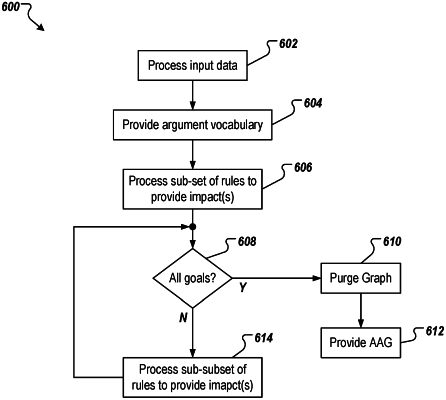
1. A computer-implemented method for executing one or more actions for cyber-security in an enterprise network, the method being executed by one or more processors and comprising:
evaluating a first sub-set of rules to provide a first set of impacts by applying one or more facts to each rule, including, for each rule, using a hash join operation to determine whether the rule results in an impact of the first set of impacts;
determining whether each goal in a set of goals has been achieved at least partially based on the first set of impacts, each goal being provided as an impact;
in response to determining that each goal in the set of goals has not been achieved, iteratively evaluating sub-sets of rules until each goal in the set of goals has been achieved;
removing one or more paths of an analytical attack graph (AAG) that is representative of potential lateral movement within the enterprise network, each of the one or more paths including one or more rules and resulting in an impact that is not a goal in the set of goals; and
storing the AAG to computer-readable memory.
|