| CPC H04L 63/08 (2013.01) [G06F 21/10 (2013.01); G06F 21/31 (2013.01); G06F 21/575 (2013.01); G06F 21/80 (2013.01); G06F 21/85 (2013.01); H04L 9/3226 (2013.01); H04L 63/062 (2013.01); H04L 63/0823 (2013.01); G06F 2221/2141 (2013.01); G06F 2221/2147 (2013.01); H04L 63/0428 (2013.01)] | 19 Claims |
|
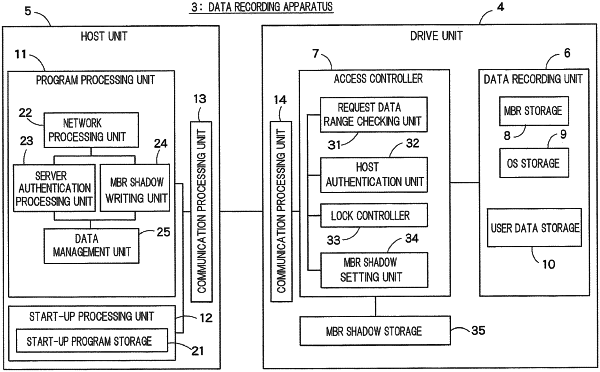
1. A method of controlling a computer executed when the computer accesses a storage of the computer before an operating system is executed by the computer at a boot-up of the computer, the storage including:
a first storage that stores the operating system, and
a second storage that stores first information indicating whether or not the first storage is locked,
the method comprising:
responsive to the first information indicating that the first storage is locked, executing an authentication process, the authentication process including receiving authentication information input by a user, sending the authentication information to a server via wireless communication, and receiving an authentication result from the server via the wireless communication, the authentication result indicating whether the authentication succeeds.
|