| CPC G06F 9/45558 (2013.01) [G06F 11/0772 (2013.01); G06F 11/1446 (2013.01); G06F 11/3037 (2013.01); G06F 12/02 (2013.01); G06F 12/1416 (2013.01); G06F 2009/45583 (2013.01)] | 20 Claims |
|
1. An information handling system, comprising:
at least one processor;
one or more non-uniform memory access nodes; and
a memory medium, coupled to the at least one processor, that stores instructions executable by the at least one processor, which when executed by the at least one processor, cause the information handling system to:
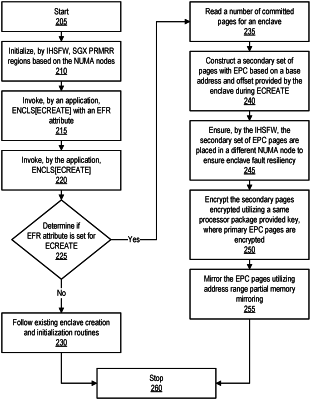
receive a request for a secure memory region from first processor instructions being executed by the at least one processor at a first processor privilege level, wherein the request for the secure memory region further comprises an enclave fault resiliency (EFR) attribute;
provide, by an operating system driver, the request for the secure memory to information handling system firmware, which is compliant with at least one of a Unified Extensible Firmware Interface (UEFI) and an Advanced Configuration and Power Interface (ACPI), via a management information exchange;
determine, based on the EFR attribute, if the request for the secure memory region further comprises a request for fault resiliency;
determine, from the one or more non-uniform memory access nodes, if a plurality of non-uniform memory access nodes exist;
if the plurality of non-uniform memory access nodes do not exist:
allocate, via the operating system driver and the information handling system firmware, a first enclave via a first volatile memory medium associated with a first non-uniform memory access node that includes the first volatile memory medium, wherein the first enclave protects at least one of second processor instructions and data from being read by and from being altered by third processor instructions executing at a second processor privilege level, higher than the first processor privilege level; and
if the request for the secure memory region further comprises a request for fault resiliency, allocate, via the operating system driver and the information handling system firmware, a second enclave via the first volatile memory medium, wherein the second enclave protects the at least one of the second processor instructions and the data from being read by and from being altered by the third processor instructions executing at the second processor privilege level;
if the plurality of non-uniform memory access nodes exist:
allocate, via the operating system driver and the information handling system firmware, the first enclave via the first volatile memory medium associated with the first non-uniform memory access node that includes the first volatile memory medium; and
if the request for the secure memory region further comprises a request for fault resiliency, allocate, via the operating system driver and the information handling system firmware, the second enclave via a second volatile memory medium associated with a second non-uniform memory access node that includes the second volatile memory medium;
encrypt, by hardware-based encryption, the at least one of the second processor instructions and the data via an encryption key that is stored by the information handling system, external to the first enclave and not accessed by the third processor instructions executing at any processor privilege level, wherein if the request for the secure memory region further comprises a request for fault resiliency, the encryption key is stored external to the first enclave and external to the second enclave;
store the at least one of the second processor instructions and the data, as encrypted by the encryption key, in the first enclave; and
if the request for the secure memory region further comprises a request for fault resiliency, mirror the at least one of the second processor instructions and the data, as encrypted by the encryption key, in the second enclave.
|