| CPC G06F 21/53 (2013.01) [G06N 20/00 (2019.01); G06F 2221/033 (2013.01)] | 15 Claims |
|
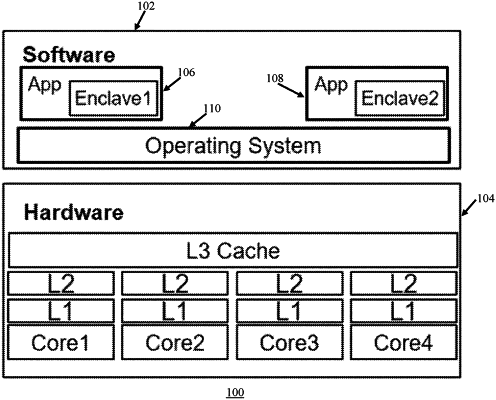
1. A method for detecting a trusted execution environment (TEE) clone application operating on a computing device, the method comprising:
based on executing a first auxiliary thread of a TEE application on the computing device, measuring a plurality of read time periods associated with a plurality of monitored cache sets within a memory cache, each of the read time periods indicating a time period that is used to read data within one of the monitored cache sets;
comparing the read time periods with a time threshold to determine one or more cache misses; and
detecting whether the TEE clone application is operating on the computing device based on the determined cache misses.
|