| CPC H04L 9/3278 (2013.01) [H04L 9/0825 (2013.01); H04L 9/085 (2013.01); H04L 9/0866 (2013.01)] | 20 Claims |
|
1. A system for controlling access to a network, comprising:
a processor;
a memory in operable communication with the processor, the memory storing instructions thereon that when executed by the processor, cause the processor to:
receive from a first node, a request to access a network;
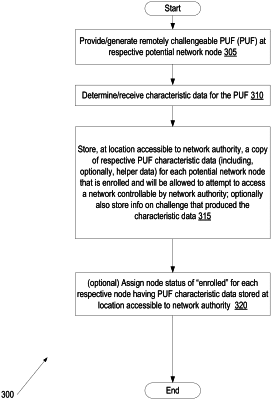
send to the first node a first challenge configured to elicit a first node fingerprint from the first node, the first node fingerprint based on the first challenge and on unique characteristic data of a physically unclonable function (PUF), at the first node;
generate an expected fingerprint for the first node based on the first challenge and on characteristic data information associated with the unique characteristic data of the PUF, wherein the processor accesses the characteristic data information from a location that is independent of and separate from the first node;
receive, from the first node, in response to the first challenge, the first node fingerprint;
authenticate the first node to the network, to allow the first node to access to the network, if the first node fingerprint matches the expected fingerprint; and
deny the first node any access to the network if the first node fingerprint does not match the expected fingerprint.
|