| CPC H04L 9/3213 (2013.01) [H04L 9/3273 (2013.01); H04L 63/123 (2013.01)] | 20 Claims |
|
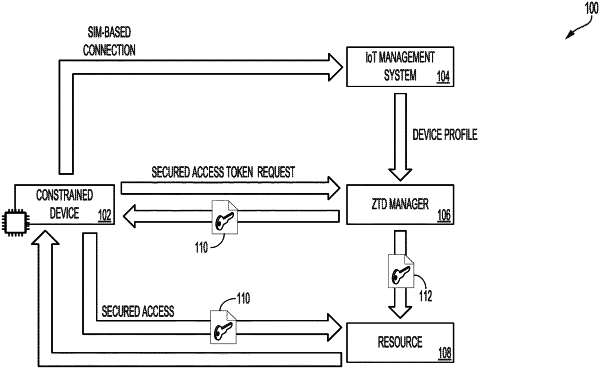
1. A computer-implemented method comprising:
receiving a first request to issue a first cryptographic token, wherein the first cryptographic token is usable to facilitate a communications session between a constrained device and a secured resource, wherein the first request corresponds to the constrained device, and wherein the constrained device lacks secured storage capabilities;
evaluating identity information corresponding to the constrained device according to a known profile associated with the constrained device;
determining that the identity information is valid;
returning a cryptographic token response, wherein the cryptographic token response includes the first cryptographic token, and wherein when the first cryptographic token is received at the constrained device, the constrained device maintains the first cryptographic token in cache memory;
receiving a second request to obtain a second cryptographic token, wherein the second cryptographic token is associated with the first cryptographic token, and wherein the second request corresponds to the secured resource; and
providing the second cryptographic token, wherein when the second cryptographic token is received at the secured resource, the secured resource uses the second cryptographic token to validate the first cryptographic token and to facilitate the communications session.
|