| CPC H04L 9/0825 (2013.01) [H04L 9/0869 (2013.01); H04L 9/0891 (2013.01); H04L 67/146 (2013.01)] | 10 Claims |
|
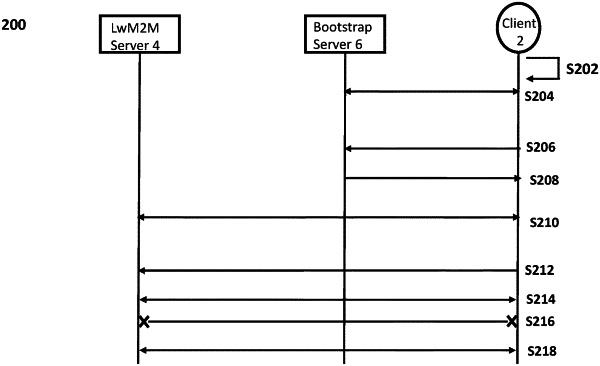
1. A computer implemented method for establishing a secure communication session between a client device and a first server, the method performed by the client device comprising:
searching and connecting to a second server utilizing a first information to locate the second server when the client device is first powered-up, wherein the first information is provisioned as part of a configuration or registration process by an owner of the client device;
obtaining, from the second server, credential data comprising a session identifier, cryptographic key data and a second information;
locating and connecting to the first server utilizing the second information;
performing a full connection handshake with the first server to establish a first secure communication session between the client device and the first server, the full connection handshake comprising:
generating first session key data based on or in response to the cryptographic key data;
when the first communication session is established:
creating a security state record defining one or more parameters for the first secure communication session, the one or more parameters including the first session key data, and associating the session identifier with the security state record, and encrypting data using the first session key data for transmission to the first server or decrypting data received from the first server using the cryptographic key data;
when the first communication session is terminated:
obtaining, from the second server or a further server, updated cryptographic key data,
generating a second session key data based on the updated cryptographic key data,
updating the security state record to include the second session key data,
performing a first resumption handshake with the first server to re-establish the first secure communication session, and
including the session identifier in the first resumption handshake to identify the security state record;
when the first secure communication session is re-established:
encrypting data using the second session key data for transmission to the first server or decrypting data received from the first server using the second session key data.
|