| CPC H04L 63/1425 (2013.01) [G06F 16/955 (2019.01); G06N 7/01 (2023.01); G06N 20/00 (2019.01); H04L 67/125 (2013.01); H04L 67/535 (2022.05)] | 15 Claims |
|
1. A system, comprising:
a processor; and
a memory that stores executable instructions that, when executed by the processor, facilitate performance of operations, the operations comprising:
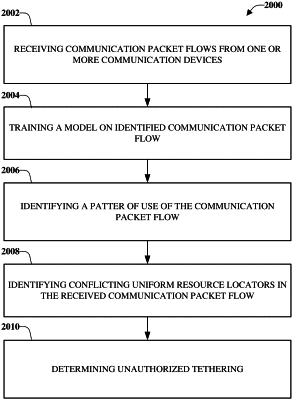
identifying a common parameter from first data that describes a first communication packet flow and second data that describes a second communication packet flow, wherein the common parameter indicates behaviors of uniform resource locators represented by the first data and the second data, wherein the uniform resource locators correlate to a plurality of different domain name systems, wherein the first communication packet flow and the second communication packet flow are associated with a user equipment, wherein tethering is not authorized at the user equipment, and wherein the identifying comprises using a model that is trained to detect the behaviors indicated by the common parameter to comprise a tethering behavior;
based on a behavior indicated by the common parameter to be the tethering behavior when the behavior indicates overlapping web pages based on the plurality of different domain name systems, determining that unauthorized tethering is occurring at the user equipment; and
based on the unauthorized tethering determined to be occurring at the user equipment, disabling a tethering option at the user equipment.
|