| CPC H04L 63/105 (2013.01) [H04L 63/0807 (2013.01); H04L 63/0815 (2013.01); H04L 63/083 (2013.01); H04L 63/0876 (2013.01); H04L 63/0884 (2013.01); H04L 63/102 (2013.01); H04L 2463/082 (2013.01)] | 24 Claims |
|
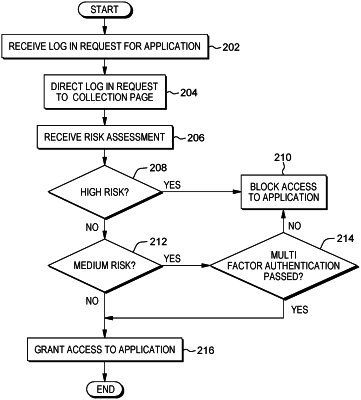
1. A computer-implemented method for authenticating a user, comprising:
receiving a login request for an application, wherein the application controls access only to a protected resource remote from a user, without an ability to control access to resources that are not the protected resource;
selecting a collection page from a plurality of collection pages stored on a server and customized to particular applications, wherein the collection page is selected based on the application for which the login request is received;
directing the login request to the collection page, wherein the collection page comprises an authentication script requesting log-in information that the application does not collect;
receiving a risk assessment based on an identity authenticated through the authentication script; and
granting a level of access to the application based on the risk assessment.
|