| CPC H04L 63/102 (2013.01) [H04L 63/083 (2013.01); H04L 63/101 (2013.01); H04L 63/108 (2013.01); G06F 9/468 (2013.01); H04L 41/0631 (2013.01)] | 20 Claims |
|
1. A system comprising:
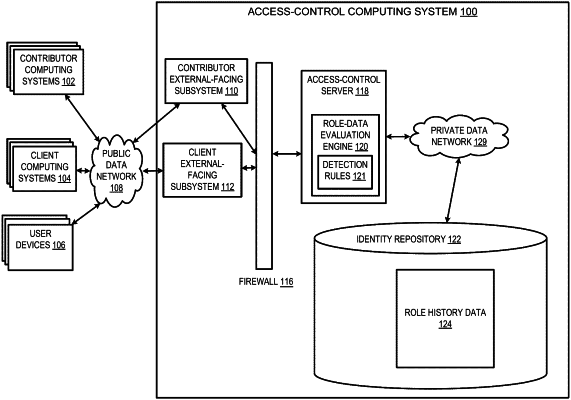
a contributor external-facing device configured for communicating with an access-control server system through a security portal and for obtaining, via communications with contributor computing systems over a public data network, role history data for entities;
a client external-facing device configured for:
receiving, from a client computing system, a query requesting that an access-verification process be applied to an access request data structure having a set of credential elements for a target entity, and
transmitting a control signal having a dynamic access-control data structure to a device in the client computing system,
in a secured part of an access verification computing system:
an identity repository to securely store the role history data obtained from the contributor computing systems; and
the access-control server system configured for:
retrieving, from the identity repository, a subset of the role history data for the target entity,
correlating values between the set of credential elements of the access request data structure and attributes from the subset of the role history data,
detecting, based on the correlation, an inconsistency between a first set of roles for the target entity identified in the access request data structure and a second set of roles for the target entity identified in the subset of the role history data,
computing a role-occupancy assessment based on durations of the target entity in roles that are identified in the second set of roles,
generating the dynamic access-control data structure comprising (i) inconsistency data describing the inconsistency and (ii) the role-occupancy assessment,
wherein the control signal is configured for causing the device of the client computing system to present an interface having (i) the role-occupancy assessment with one or more visual indicators of a security assessment associated with the durations of the target entity in the roles and (ii) a timeline view that visually depicts the inconsistency data.
|