| CPC H04L 63/10 (2013.01) [G06F 21/6245 (2013.01); G06K 19/06037 (2013.01); G08B 5/22 (2013.01); H04L 63/0884 (2013.01); H04W 12/35 (2021.01)] | 11 Claims |
|
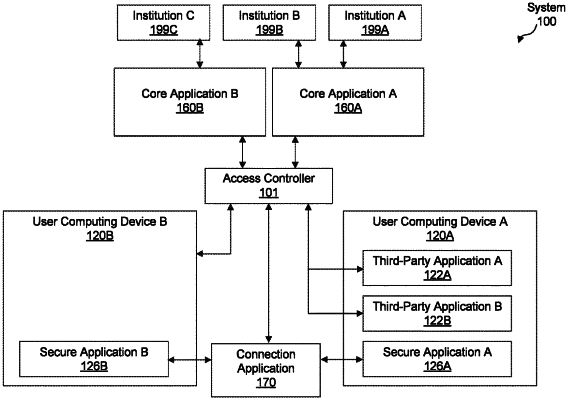
1. A method for improving security of computer-based transactions, comprising:
providing security software between a core application and a third-party application, the third-party application executing on a mobile device, wherein the security software prevents the third-party application from unauthorized access to the core application and is independent from the core application;
receiving, by the security software, a command from the third-party application to access the core application;
receiving, by the security software, an identifier associated with the command, wherein the identifier is one of a two-dimensional bar code, a numerical value, or a string generated by the security software and transmitted by the third-party application;
determining, by the security software, a secure application associated with the identifier, the secure application executing on the mobile device;
transmitting an authorization request to the secure application, the authorization request identifying the command and the third-party application;
determining, by the security software based on a response from the secure application, whether the authorization request is approved;
allowing, by the security software, the third-party application to access the core application in response to determining that the authorization request is approved, wherein the allowing comprises transmitting, by the security software, the command to the core application, wherein the core application is associated with an institution, and wherein the core application executes the command;
preventing, by the security software, the third-party application from accessing the core application in response to determining that the authorization request is not approved; and
in response to allowing the third-party application to access the core application:
receiving, by the security software, user data associated with a user from the core application based on the command; and
transmitting, by the security software, the user data to the third-party application.
|