| CPC G06F 21/566 (2013.01) [G06N 20/00 (2019.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer implemented method for protecting control device objects of a system driver in a computer system, the method executed on a processor, the method comprising:
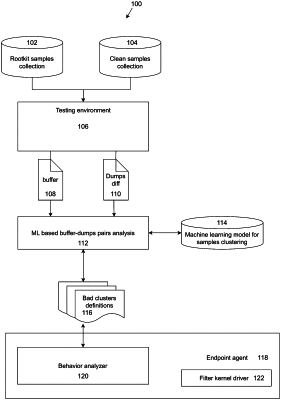
collecting, in a testing environment, a first input/output (“I/O”) buffer to the system driver;
collecting, in a testing environment, a first system memory dump before execution of the first I/O buffer by the system driver;
collecting, in a testing environment, a second system memory dump during execution of the I/O buffer by the system driver;
identifying a difference between the first and second system memory dumps;
pairing the first I/O buffer with the difference;
repeating the foregoing steps until a plurality of first I/O buffers are paired with a plurality of differences;
training a machine learning model for samples clustering using the plurality of paired first I/O buffers and differences;
identifying a set of clusters definitions, wherein at least one of the clusters includes samples related to rootkits;
collecting, outside the testing environment, a second I/O buffer to the system driver;
passing the second I/O buffer to the machine learning model for clustering; and
allowing the second I/O buffer to pass to the system driver for execution if the machine learning model determines that the second I/O buffer is not clustered with a rootkit-related cluster definition.
|