| CPC G06F 21/56 (2013.01) [G06F 9/542 (2013.01); G06F 17/18 (2013.01); G06N 3/08 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
receiving process data from a client computer system based on activity and behaviors of the client computer system;
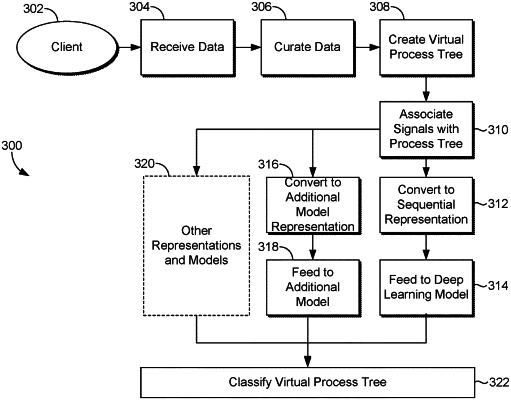
generating a process tree based on parent and child relationships associated with the process data, wherein the process data is associated with a plurality of processes;
associating, in the process tree, each of the plurality of processes with a corresponding signal associated with signal data;
based on the process tree comprising the parent and child relationships and a chronology of execution of the plurality processes having corresponding signals, generating a vector of a sequence of events, wherein the vector is associated with scoring a probability that the sequence of events from the vector is malicious,
the vector is a representation of the process tree comprising a first process that produces a first signal at a first time and a second process that produces a second signal at a second time, the first process and the second process have a parent and child relationship;
inputting the vector into a trained model associated with registry-related features of a plurality of sequences of events that indicate malicious activity, the registry-related features of the plurality of sequences of events correspond to registry-related features in training process data, training signal data, and training chronology of execution and relationship between processes data,
the trained model is configured to evaluate the vector for potentially malicious activity;
based on inputting the vector into the trained model, generating a score that indicates whether the sequence of events represented by the vector is malicious, wherein the score is generated using the trained model, the parent and child relationships, chronology of execution of the plurality processes represented in the in the sequence of events of the vector, and registry-related features associated with the sequence of events; and
based on the score satisfying an alert threshold, causing a security risk mitigation action.
|