| CPC B60W 60/00188 (2020.02) [G08G 1/20 (2013.01); H04W 12/009 (2019.01); H04W 12/50 (2021.01); H04W 12/67 (2021.01); H04L 9/0643 (2013.01)] | 20 Claims |
|
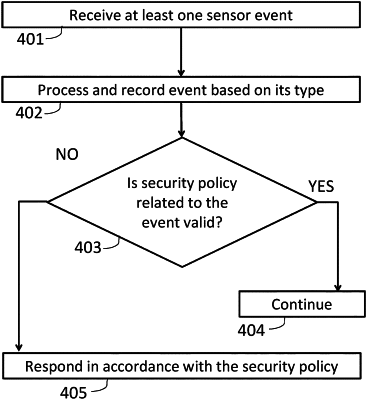
1. A security system comprising:
a security layer embedded in a component connected to an in-vehicle network and adapted to:
detect an occurrence of an event related to exploitation of the component based on a deviation from an expected behavior, wherein a deviation is detected based on identifying the occurrence of an unexpected sequence of events;
wherein the occurrence of an unexpected sequence of events is at least one of:
an execution of a sequence of programs,
a consecutive or repetitive executions of the same program,
a calling of a set of functions or APIs in a specific sequence or order, and
accessing a set of resources in a specific sequence or order; and
if a deviation is detected, then log the event.
|