| CPC H04L 9/3252 (2013.01) [H04L 9/0825 (2013.01); H04L 9/0861 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 9/3066 (2013.01)] | 15 Claims |
|
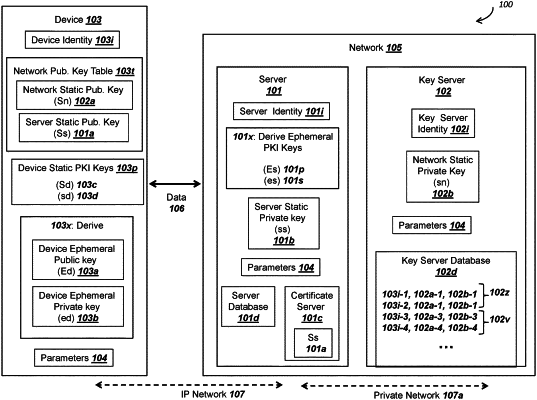
1. A method for a wireless device to securely communicate with a network, the method performed by the wireless device, the method comprising:
a) storing in a nonvolatile memory a device static private key and a device identity;
b) storing in a random access memory, a network public key and a server public key, wherein the network public key and the server public key are unique for the wireless device;
c) generating a random number from (i) device transducer data and (ii) a random number generator, the random number comprising a device ephemeral private key corresponding to a device ephemeral public key;
d) generating, by a system-on-a-chip (SoC), a digital signature for at least the device ephemeral public key using the device static private key;
e) deriving, by the SoC, a first symmetric ciphering key from a first elliptic curve Diffie Hellman (ECDH) key exchange with the device ephemeral private key and the network public key;
f) deriving, by the SoC, a second symmetric ciphering key from a second ECDH key exchange with the device ephemeral private key and the server public key;
g) encrypting, by the SoC, at least the device identity with the first symmetric ciphering key to generate a first ciphertext;
h) transmitting, by a radio in the wireless device and to the network, the device ephemeral public key, the first ciphertext, and the digital signature, wherein the SoC sends the device ephemeral public key and the first ciphertext to the radio in the wireless device using a system bus;
i) receiving, by the radio in the wireless device and from the network, a double-encrypted response;
j) conducting, by the SoC, a first decryption of the double-encrypted response with the second symmetric ciphering key in order to read a second ciphertext, wherein the SoC receives the double-encrypted ciphertext from the radio in the wireless device using the system bus; and
k) conducting, by the SoC, a second decryption of the second ciphertext with the first symmetric ciphering key in order to read a plaintext response.
|