| CPC H04L 9/0891 (2013.01) [G06F 9/45558 (2013.01); G06F 21/72 (2013.01); G06F 2009/45579 (2013.01); G06F 2009/45587 (2013.01)] | 18 Claims |
|
1. A host server computer comprising:
an interconnect;
a host memory coupled to the interconnect;
a set of processor cores including a first processor core and a second processor core, the set of processor cores configured to execute instructions stored in the host memory, wherein execution of the instructions causes the set of processor cores to:
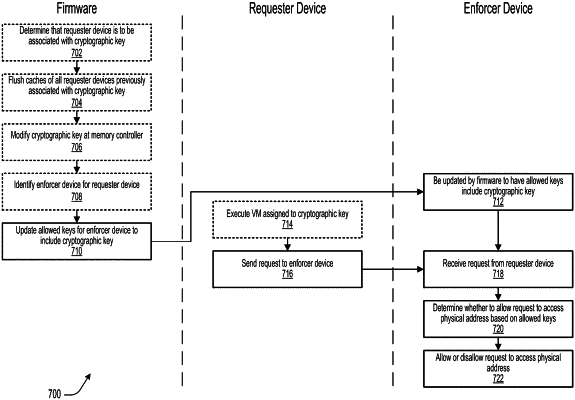
execute a first virtual machine (VM) using the first processor core and a second VM using the second processor core, wherein the first VM is assigned to a first cryptographic key, and wherein the second VM is assigned to a second cryptographic key; and
send a first request from the first processor core toward the interconnect for the first VM and a second request from the second processor core toward the interconnect for the second VM, wherein the first request includes a first physical address in the host memory and the second request includes a second physical address in the host memory; and
a set of enforcer devices coupled between the set of processor cores and the interconnect, the set of enforcer devices including a first enforcer device for the first processor core and a second enforcer device for the second processor core, wherein the first enforcer device is configured to receive the first request and determine whether to allow the first request to access the first physical address via the interconnect based on a first set of allowed keys, and wherein the second enforcer device is configured to receive the second request and determine whether to allow the second request to access the second physical address via the interconnect based on a second set of allowed keys.
|