| CPC H04L 63/1416 (2013.01) [G06F 21/52 (2013.01); G06F 2221/034 (2013.01)] | 12 Claims |
|
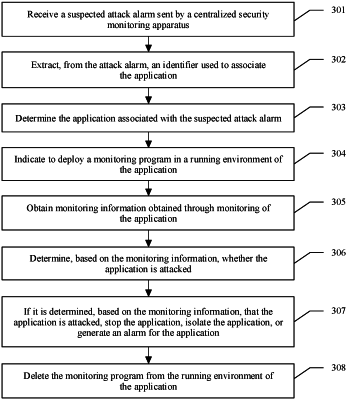
1. A security management method carried out on behalf of an application deployable in a multi-machine operating environment, the method comprising:
receiving a suspected attack alarm from a centralized security monitoring apparatus;
extracting, from the suspected attack alarm, an identifier used to associate the application;
determining, in accordance with the identifier, the application associated with the suspected attack alarm;
issuing, in accordance with the receiving a suspected attack alarm and the determining the application associated with the suspected attack alarm, a request for a monitoring program to be deployed to an operating environment of the application, wherein the monitoring program is executed in the operating environment to generate a monitoring information during operation of the application;
obtaining, in accordance with the issuing the request and by executing the monitoring program deployed to and executed in the operating environment, the monitoring information of the application;
determining, in accordance with the obtaining and based on the monitoring information of the application, the application has been attacked;
stopping or isolating, in accordance with the determining the application has been attacked, the application; and
deleting, after the determining the application has been attacked, the monitoring program from the operating environment of the application.
|