| CPC G06F 21/64 (2013.01) [G06F 21/52 (2013.01); G06F 21/57 (2013.01)] | 11 Claims |
|
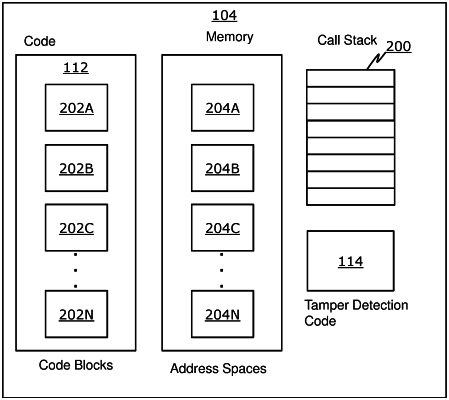
1. A method for detection of tampering in an executable code of an application, the executable code including one or more code blocks, the method comprising:
monitoring execution of the executable code, the execution involving accessing one or more address spaces, wherein an address space is associated with respective ones of the one or more code blocks;
determining if an address space associated with one of the one or more code blocks is within the executable code by comparing information about the accessed address space with information about an allowed address space for the one or more code blocks; and
if the accessed address space is directed to an address outside the executable code, immediately terminate execution of the executable code;
wherein monitoring execution of the executable code further comprises:
executing a tamper detection code that is inserted in the executable code, wherein the executable code comprises at least one read-only segment containing information related to the one or more allowed address spaces, and wherein the method includes executing the tamper detection code to load the information related to the one or more allowed address spaces from the at least one read-only segment; and
wherein the tamper detection code is configured to retrieve a starting address of the at least one read-only segment as an application program of the executable code starts to execute and store the starting address as the allowed address space.
|